LoRa IoT Device Firmware Update through Cloud Over-the-Air Interfaces
Firmware is an integral part of devices, which refers to the software that instructs the hardware to function and commu- nicate with other software running on a device. Firmware updates are necessary to address security or performance issues during the lifetime of IoT (Internet of Things) devices. Over-the-Air (OTA) updates enable firmware updates to be completed remotely and securely, without the need to re- move devices from their deployment.
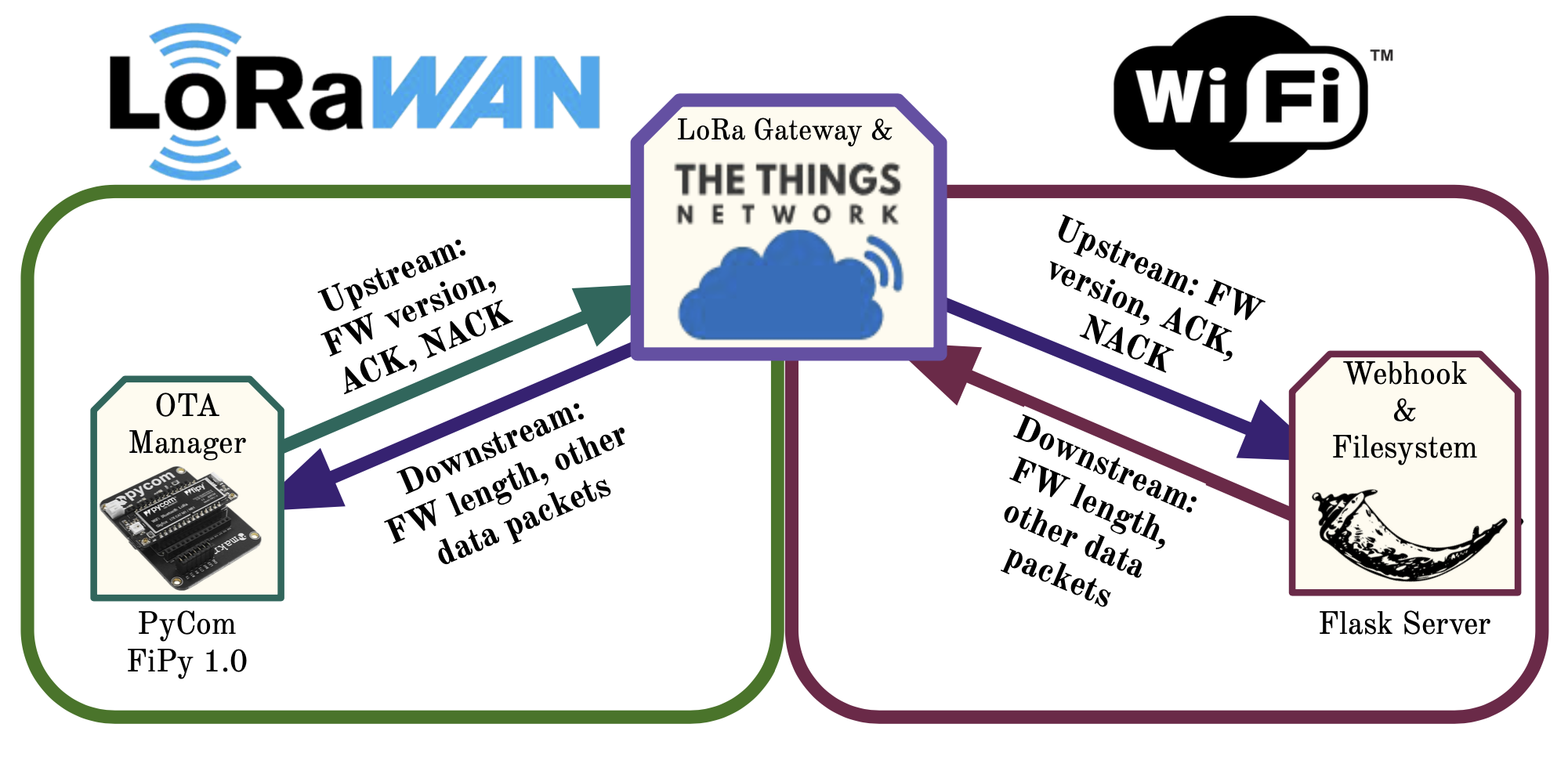
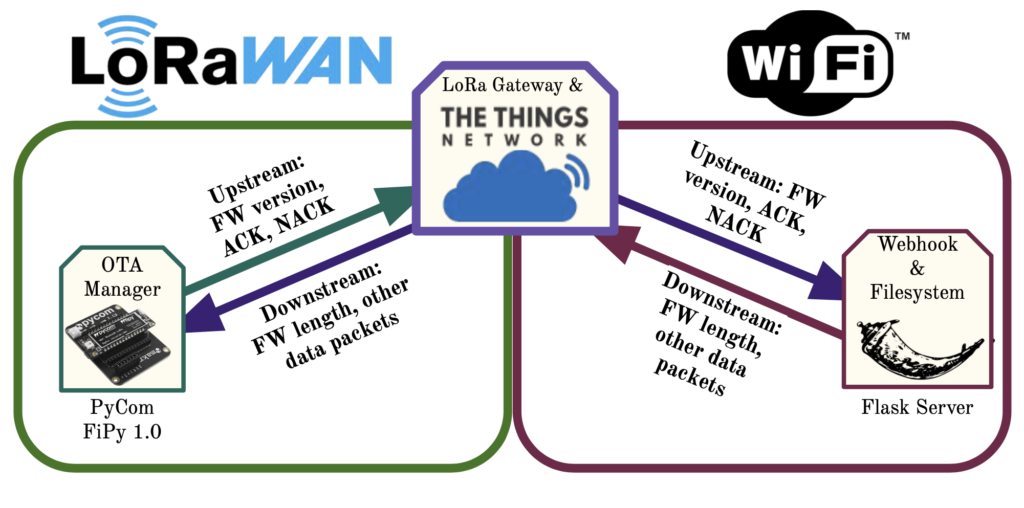
This paper introduces a LoRa (Long Range) OTA procedure to enable cloud-based resources to initiate and complete updates to LoRa-connected IoT devices. This differs from existing OTA over LoRa solutions by allowing the LoRa gateway to simply push updates from upstream servers man- aging the deployment of devices. Upstream servers expose APIs to allow devices communicating over a TTS instance to initiate the OTA procedure. A PyCom FiPy was chosen as the IoT device on which to perform OTA.
Background
- LoRa is a long-range, low-power networking protocol that allows IoT devices to communicate securely. It allows devices to be managed by base stations while allowing them to function for years without depleting on-board batteries.
- Over-the-Air (OTA) updates have enabled security patches and mission-critical updates to be delivered to increasingly important IoT devices.
- As part of managing these devices, it makes sense to be able to carry out OTA updates over LoRa.
- Our Goal: Enable LoRa OTA between Cloud and LoRa Devices.
Procedure:
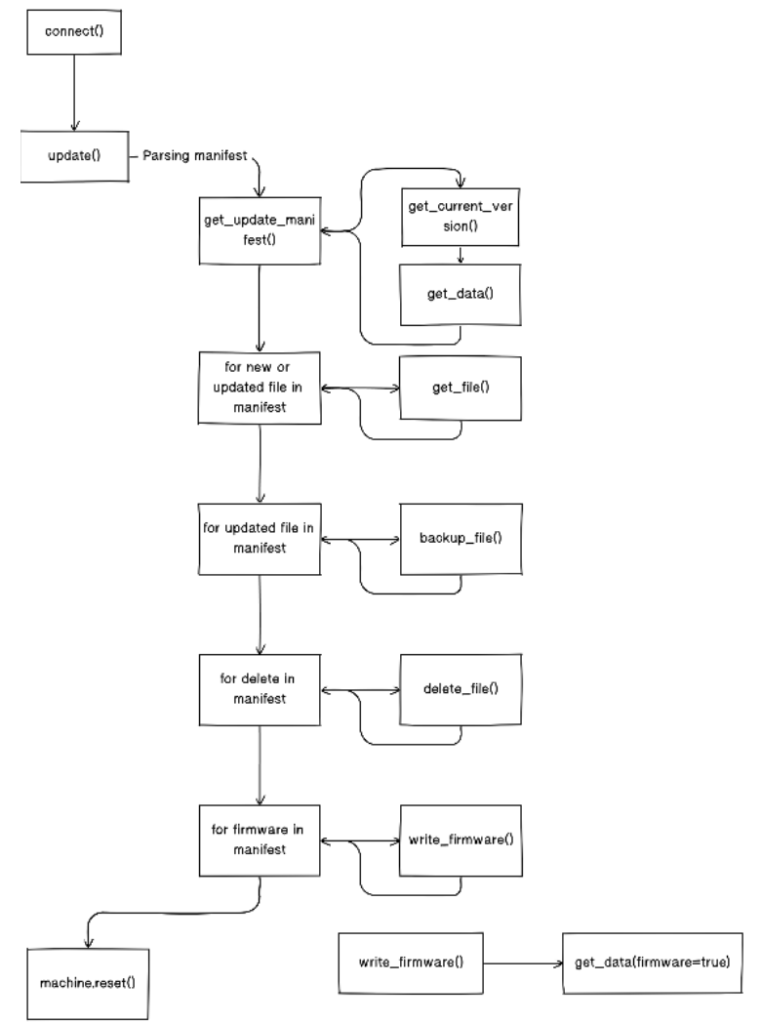
- Device connects with server over WiFi
- Device requests manifest
- Server sends builds & sends manifest
- Device receives manifest and updates application and firmware files accordingly
- Requests files that are not on device from server
- Backs up old files that needs to be updated
- Deletes obsolete files per manifest directives
- For every firmware file, write firmware to OTA partition on device and set flag to boot from OTA instead of partition
- Machine resets to complete update
Implementation Steps
Setup Configurations
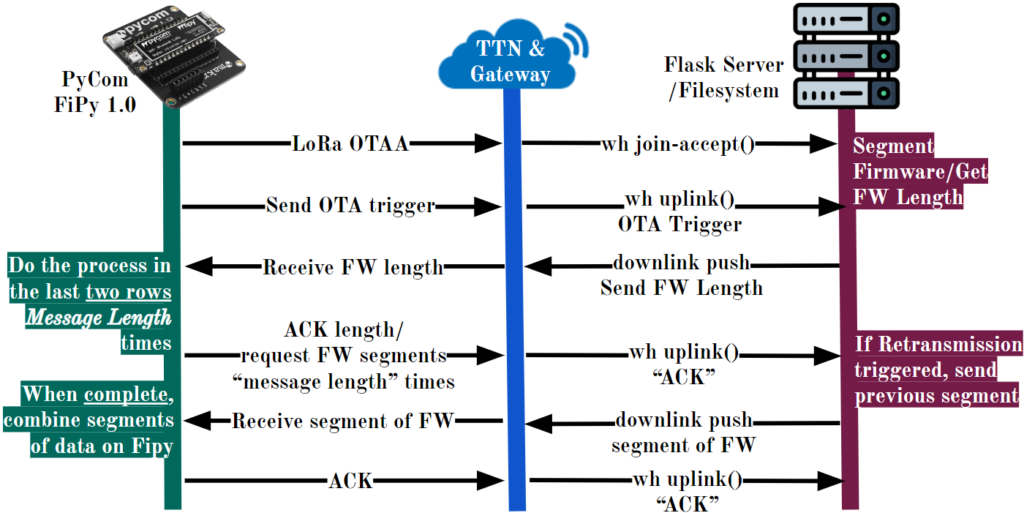
LoRa Socket:
- LoRaWAN Mode – US-compliant bandwidth, channels, and frequencies (Zone: US915)
- LoRa OTAA (Over the Air Authentication)
- Blocking set – device waits for packets to be received
- Socket timeout set to 15 seconds – client triggers retransmission after 15 seconds of not receiving an expected packet
Triggers/ACKs/NACKs:
- No OTA protocol for LoRa: start, stop, data format etc.
- Example WiFi OTA code only send arbitrary bytes as trigger – we do the same thing
- Using arbitrary bytes
- LoRa also does not have ACKs – we set our own bytestring to ACK
- After server receives ACK, disposes of the last binary chunk / the last packet sent
- LoRa also does not have NACKs – we set another bytestring to serve as NACK
- After server receives NACK, retransmits the last binary chunk / the last packet sent
- Use of NACK is not ideal, but it works very well! Retransmission is guaranteed in case of packet drop/transmission failure
Data Segmentation:
- Data segmentation of the binary is done on the server
- Our current chunk size is 40 bytes
Achieved:
- Transfer of files from webserver to LoRa device
- Concatenation of chunks on end device to a file
- Writing of files into OTA (firmware) partition
- Retransmission of the last message from the server to the device if the device times out
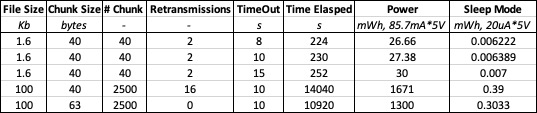
Demo